Principle of Encryption
On starting the Humber cipher machine, the operator receives the message "Search for files to encrypt? (y/n)". If "n" is selected the control will move on to decryption. If "y" is selected, Humber then creates a list of all the files in the "messages" folder. If there are any files in the "messages" folder, the first is offered for encryption via the prompt "Encrypt filename (y/n)", where filename is the name of the first unmatched file. If the operator accepts the file, the prompt "Generating hash for encryption" appears followed by the prompt "Use Stream Mode? (y/n)". Rejection of Stream Mode results in Hex Mode being used for the cipher. Hex Mode will cause the output to appear as hexadecimal pair representations of the output stream. Once the choice has been made, encryption proceeds immediately. A typical operator's control window is shown in Figure 2.
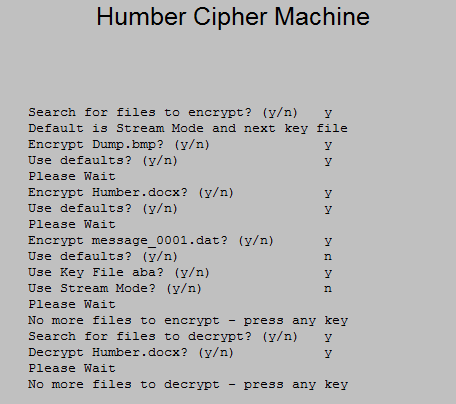
Each message file is offered in turn. If the operator rejects a file, the next one is offered until there are no more unencrypted files. The same procedure is followed for decryption, this time using the files in the "cripin" folder.