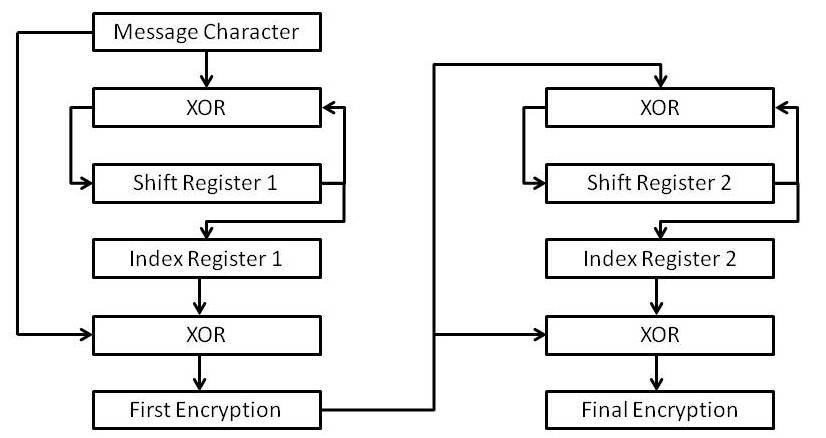
Encrypting the Data
The two stages of encryption are identical. For each stage of the 2-stage encryption the following notation is used (the subscript i corresponds to the i th character from the plain language message):
Ci = the ASCII value of the i th enciphered character;
Ri = the value of the index register element used for encrypting or decrypting the ith character
R( j) = the value of the j th element of the index register;
S( j) = the j th element of the shift register;
Si = the value of S(1) for the i th character;
Pi = the ASCII value of the i th plaintext character.
For the first stage of encryption, the first encryption is represented by Ci, while for the second stage, the first encryption is represented by Pi. The encryption process begins by using a bitwise XOR function to combine the ASCII value of each plain language character in turn with the contents of the appropriate element of the index register, indicated by the value of Si :
This produces the enciphered character, Ci. The XOR function is also used to combine the same plain language character with the contents of Si, the result of which is added to the shift register as the next value of S(256)i+1, after a SHIFT RIGHT LOGICAL operation on the shift register. The value of Si used for the encryption is overwritten and cannot be recovered:
In practise, if there were a large number of repeated identical characters in the plain language text, a pattern would emerge in the output. The pattern could be used to identify the keys, if the repeating character can be discovered. Therefore an additional step is incorporated whereby a PRNG generates a random number between 0 and 255 to be combined with the result of Equation (3)
where Ri is the random number. Thus Si is a number used once only (nonce). The random number generator seed does not need to be secure because its only function is to mask the effect of repeated characters.
The purpose of the shift register process is to ensure there is no traceable connection between S(256)i+1 and the enciphered character Ci. The whole encryption process is illustrated by Figure 6.